Cybersecurity in ASEAN is changing faster than most organizations realize.
Companies still invest heavily in endpoint antivirus, perimeter firewalls, and cloud monitoring — but attackers have already moved to a different battlefield.
That battlefield is API communication.
APIs sit at the center of every modern system: authentication, mobile apps, payments, logistics, HR systems, banking, healthcare records, and even school portals. Without APIs, nothing works.
And because APIs are the lifeline of digital infrastructure, they have become the number one attack vector in 2025.
1. APIs Travel Inside Trusted Channels — Making Them Invisible to Firewalls
A firewall is designed to protect ports, IP ranges, and protocols.
But APIs don’t travel in dangerous-looking traffic. They travel inside the safest-looking connection possible:
Encrypted HTTPS
To a firewall, a malicious API call looks like:
GET /api/v1/data
POST /auth/token
PUT /records/update
There is nothing suspicious in the protocol.
The danger is inside the request, not in the port or IP.
+ Firewalls protect ports.
+ API security protects behaviour.
This is why 100% of major API breaches bypass traditional firewalls completely.
2. API Attacks Have Exploded — And Most Are Automated
According to global cybersecurity reports:
83% of cloud breaches begin at the API layer
API traffic now represents 70% of internet traffic
Shadow APIs are responsible for 60% of unknown exposures
Hackers now use automated tools such as:
Xpanse
ShadowScan
GraphRider
JWTBreaker
APIStorm
These tools can attack thousands of APIs per minute — all without alerting traditional firewalls.
3. The Most Common API Breaches in 2025
1) Broken Object Level Authorization (BOLA)
Attackers change ID numbers:
/api/user/101 → /api/user/102
If access is not validated, your data leaks instantly.
2) Broken Authentication
Weak tokens, leaked API keys, or session errors.
3) Mass Assignment
Sending unexpected fields:
role=admin
4) Replay attacks
Reusing authorization tokens.
5) Scraping and enumeration
Bots map your entire API structure.
6) Shadow APIs
Forgotten endpoints no one monitors anymore.
7) JSON injection
Manipulating JSON bodies to alter logic.
A firewall sees none of this.
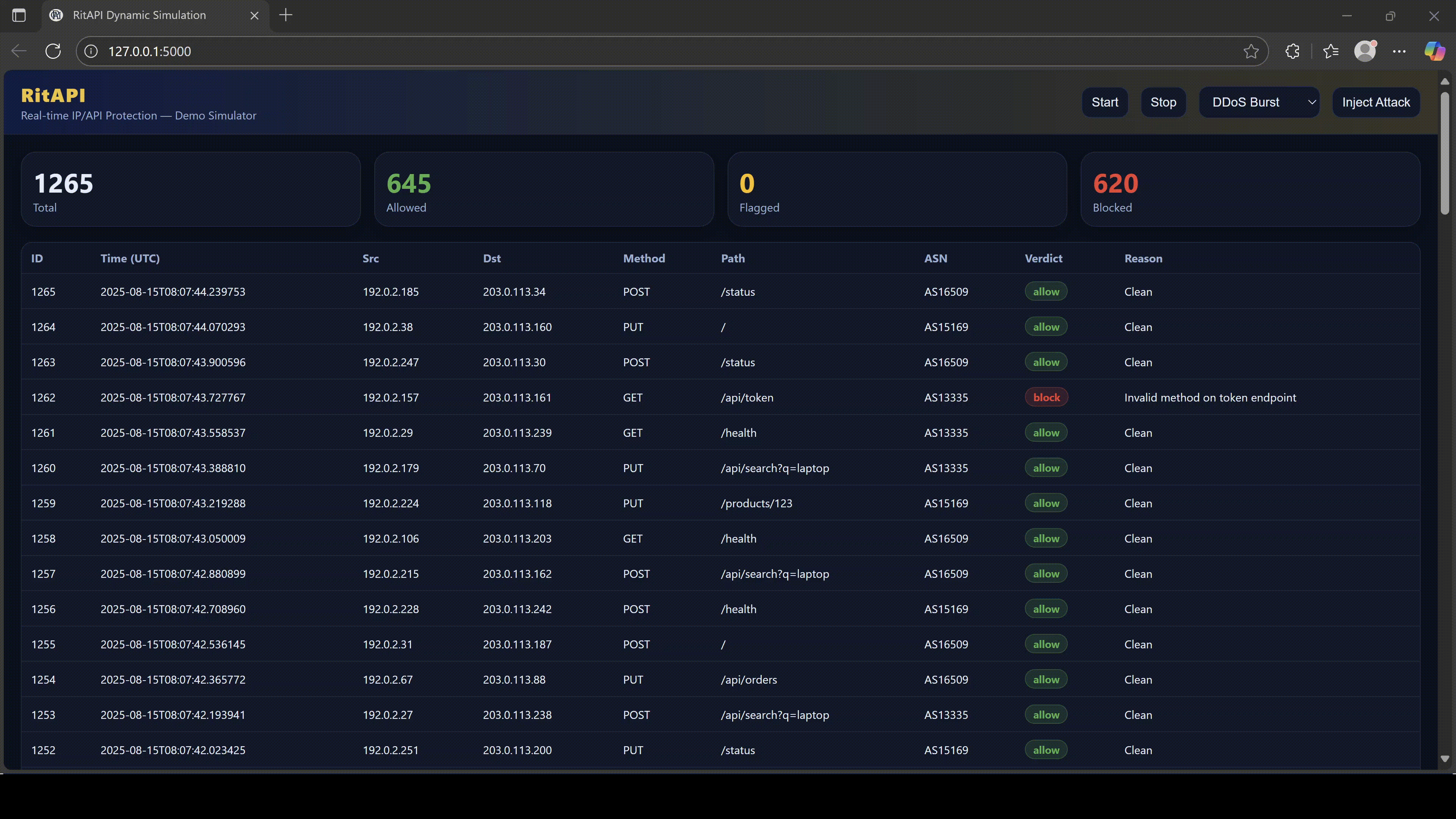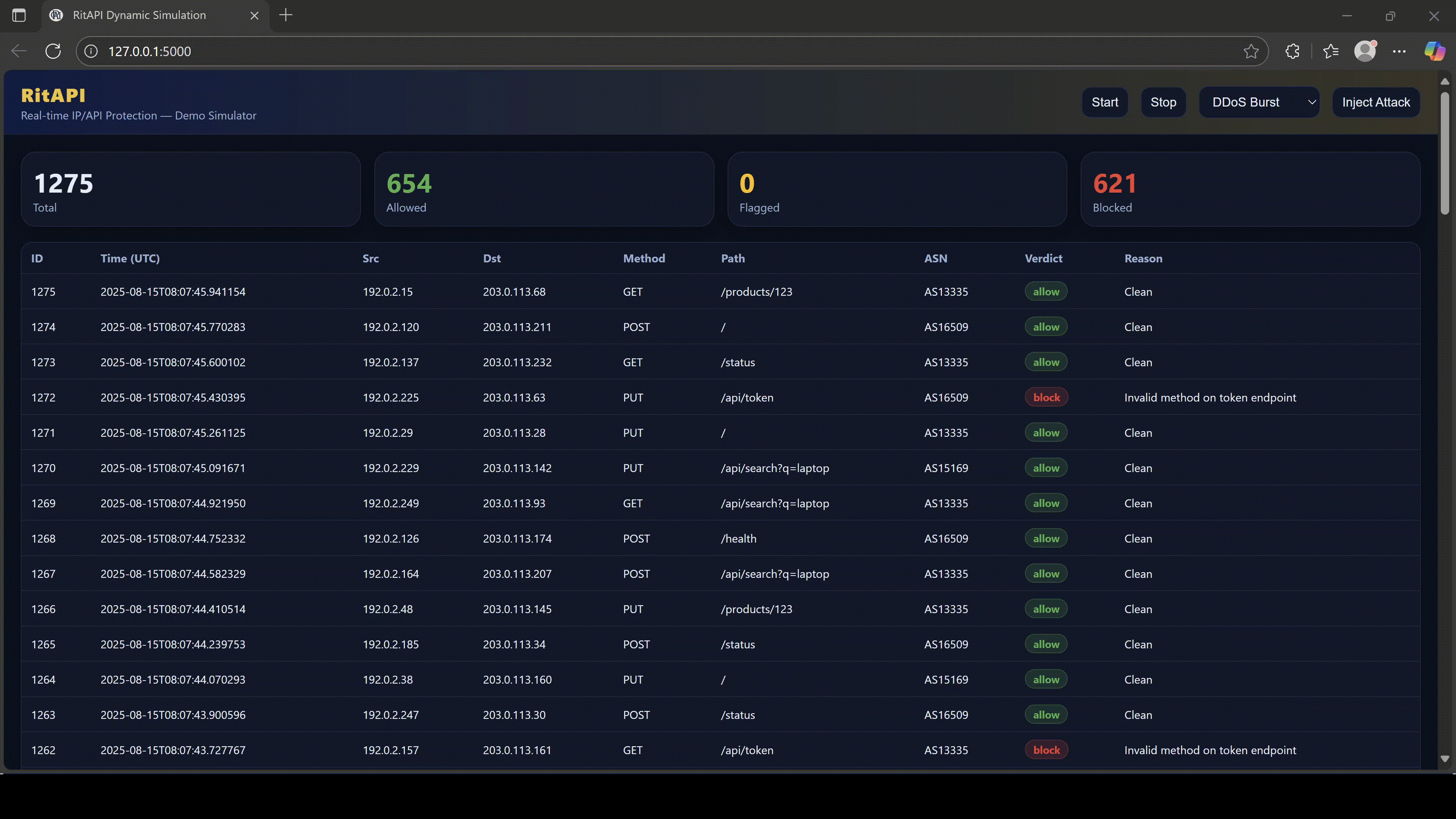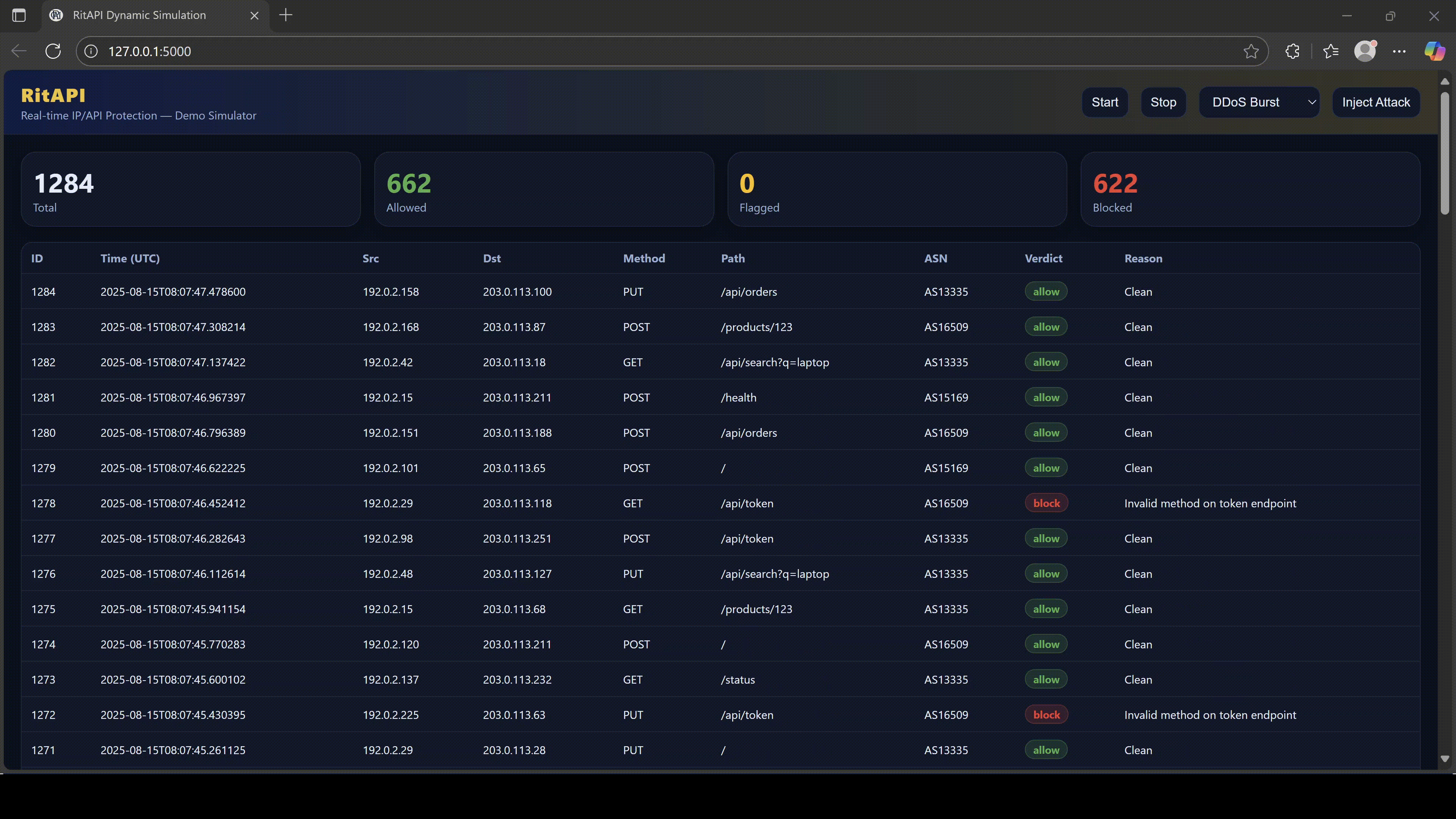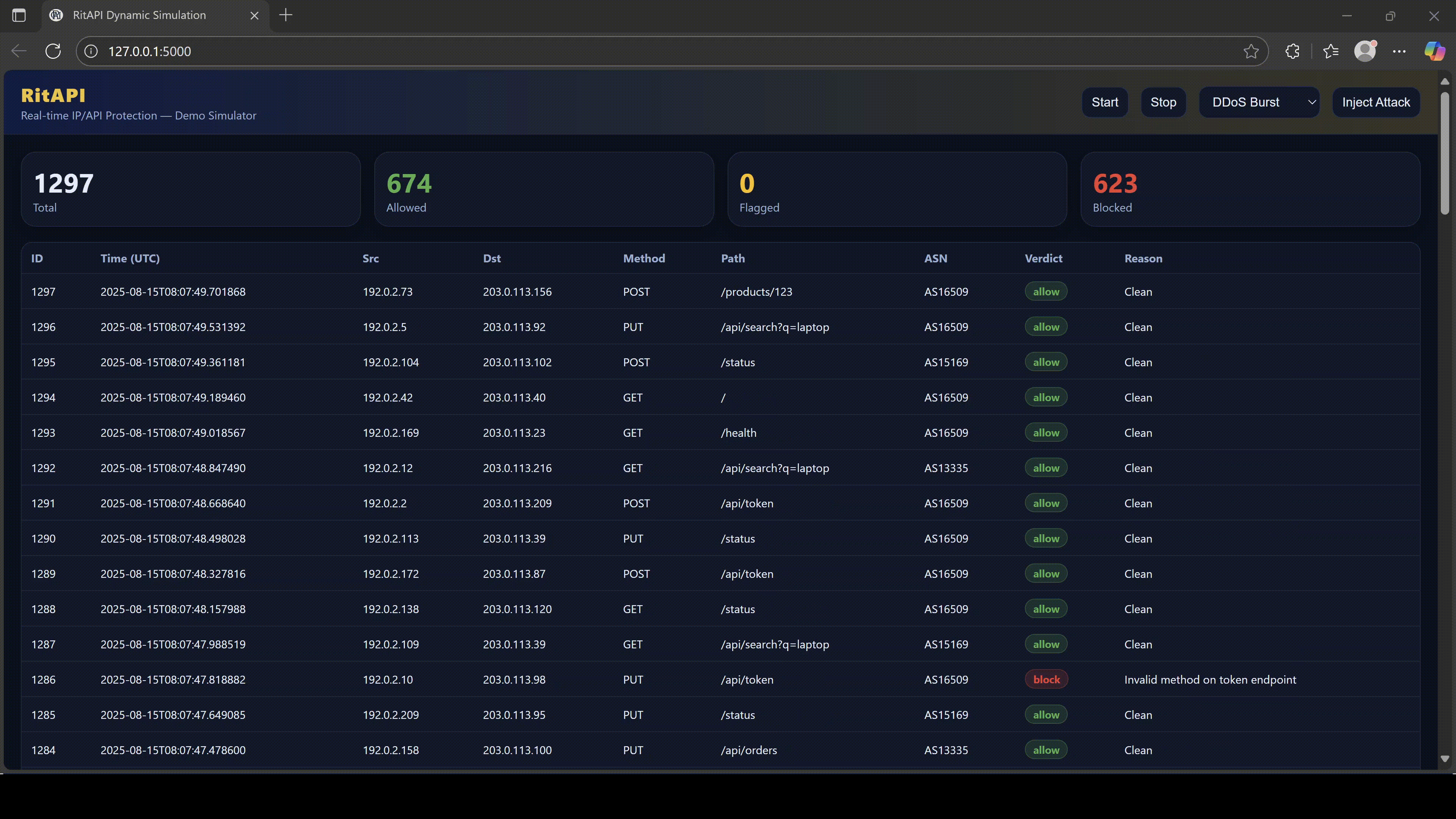
RitAPI sees everything.
4. Why RitAPI Is Essential for Modern Protection
RitAPI is an API security shield designed for Southeast Asia’s digital infrastructure.
It analyzes every connection, every JSON body, every session, and every decision.
RitAPI protects you with:
✓ API anomaly detection
✓ Advanced JSON/GraphQL inspection
✓ Token and session scoring
✓ IP/ASN trust rating
✓ TLS fingerprinting
✓ Supply chain behaviour mapping
✓ Bot and machine-to-machine detection
RitAPI does what firewalls cannot:
Protect the data IN the tunnel, not just the tunnel itself.
5. Real Examples of API Breaches RitAPI Can Prevent
Case 1 — School LMS Data Leak
A student changes URL IDs and accesses other students' data.
RitAPI blocks this instantly.
Case 2 — Hospital EMR API Misuse
A vendor API is abused to extract patient records.
RitAPI detects abnormal access volume.
Case 3 — Banking API Replay Attack
A stolen JSON Web Token (JWT) is reused.
RitAPI rejects the replay and alerts.
Case 4 — Shadow API in an old mobile app
Forgotten endpoint exposed credit data.
RitAPI maps all APIs and reports unmonitored routes.
6. Firewalls Are Still Needed — But No Longer Enough
The modern stack requires:
Firewall (Archangel 2.0)
AI Behaviour Firewall (MiniFW-AI)
API Security Layer (RitAPI)
This is why companies across Indonesia deploy:
Archangel 2.0
MiniFW-AI
RitAPI
= Complete Digital Immune System
Conclusion: API Security Is Now the Core of Cybersecurity
If APIs are not protected, your company, school, or hospital is already exposed — even if you have the best firewall in the world.
RitAPI closes the blind spot attackers rely on.